Word for Microsoft 365 Word for Microsoft 365 for Mac Word 2021 Word 2021 for Mac Word 2019 Word 2019 for Mac Word 2016 Word for iPad Word for iPhone Word for Android tablets Word for Android phones More. Less
Information Rights Management (IRM) helps you prevent sensitive information from being printed, forwarded, or copied by unauthorized people. The permissions are stored in the document where they are authenticated by an IRM server.
Using IRM in Microsoft 365, you can rights manage XML Paper Specification (.xps) files and the following Word file types:
To use IRM in Microsoft 365, the minimum required software is Windows Rights Management Services (RMS) Client Service Pack 1 (SP1). The RMS administrator can configure company-specific IRM policies that define who can access information and what level of editing is permitted for an e-mail message.
For example, a company administrator might define a rights template called "Company Confidential," which specifies that an e-mail message that uses that policy can be opened only by users inside the company domain.
The first time you try to open a document with restricted permission, you must connect to a licensing server to verify your credentials and download a use license. The use license defines the level of access that you have to a file. This process is required for each file that has restricted permission.
Downloading permissions requires that Microsoft 365 send your credentials, which includes your e-mail address, and information about your permission rights to the licensing server. Information contained in the document is not sent to the licensing server.
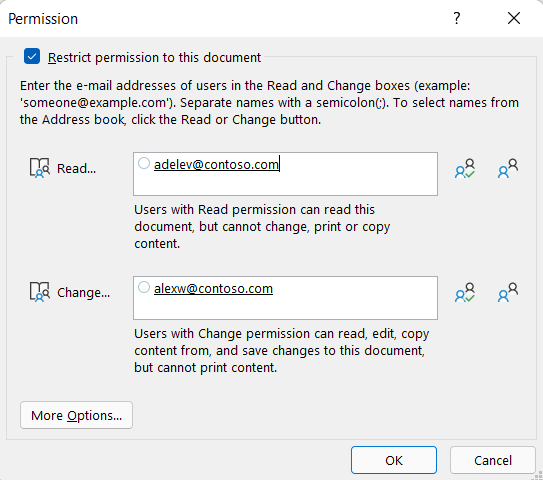
IRM lets you apply restrictions on a per-user, per-file, or per-group basis (group-based permissions require Active Directory).
For example, in a document Ranjit creates, he might give Adele permission to read but not change it. and give Alex permission to edit the document. Ranjit might also decide to apply a five-day limit to both Adele and Alex's access to the document.

Note: Your choices might be limited if an administrator has set custom permission policies that individuals can't change.
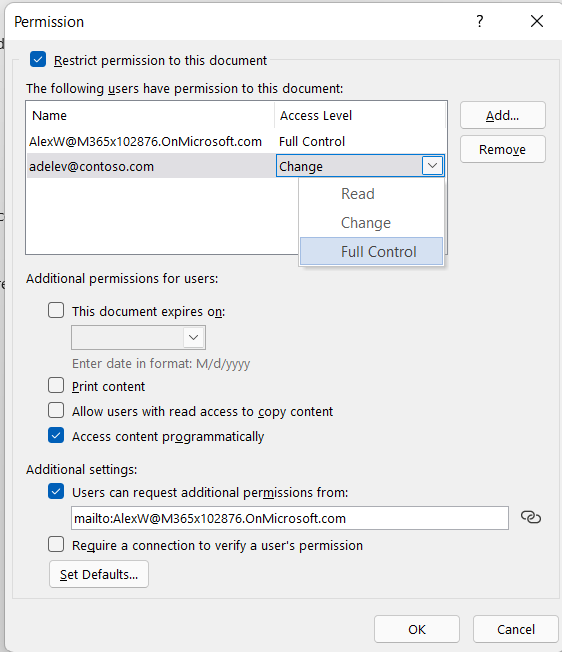
After permission for a document has expired for authorized users, the document can be opened only by the author or by users with Full Control permission to the document. Authors always have Full Control permission.
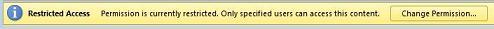
After you assign permission levels, select OK. The Message Bar appears, which indicates that the document is rights-managed. If you must make any access permission changes to the document, select Change Permission.
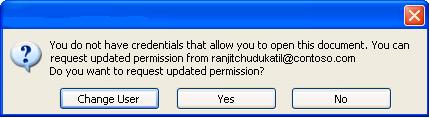
If a document that has restricted permission is forwarded to an unauthorized person, a message appears with the author's e-mail address or Web site address so that the unauthorized person can request permission for the document.
To view rights-managed content that you have permissions to by using Microsoft 365, just open the document.
If you want to view the permissions you have, either select View Permission in the Message Bar or choose This document contains a permissions policy

IRM in Office for Mac provides three permission levels.
Do any of the following:
Set permission levels manually
Note: If you do not select Save password in Mac OS keychain, you might have to enter your user name and password multiple times.
Use a template to restrict permission
An administrator can configure company-specific IRM policies that define who can access information permissions levels for people. These aspects of rights management are defined by using Active Directory Rights Management Services (AD RMS) server templates. For example, a company administrator might define a rights template called "Company Confidential," which specifies that documents that use that policy can be opened only by users inside the company domain.
Change or remove permission levels that you have set
If you applied a template to restrict permission, you can't change or remove permission levels; these steps only work if you have set permission levels manually.
Set an expiration date for a restricted file
Authors can use the Set Permissions dialog box to set expiration dates for content.
Allow people with Change or Read permission to print content
By default, people with Change and Read permission cannot print.
Allow people with Read permission to copy content
By default, people with Read permission cannot copy content.
Allow scripts to run in a restricted file
Authors can change settings to allow Visual Basic macros to run when a document is opened and to allow AppleScript scripts to access information in the restricted document.
Require a connection to verify permissions
By default, people have to authenticate by connecting to the AD RMS server the first time that they open a restricted document. However, you can change this to require them to authenticate every time that they open a restricted document.
Remove restrictions
In the iOS versions of Microsoft 365, any IRM-protected files that you receive will open if you are signed in with an account that has permissions to the file. When you open an IRM-protected file you will see an information bar at the top that offers to let you view the permissions that have been assigned to this file.
If you're a Microsoft 365 Subscriber with Azure Rights Management and your IT-department has defined some IRM templates for you to use, you can assign those templates to files in Office on iOS.
To protect a file tap the edit button
in your app, go to the Review tab and tap the Restrict Permissions button. You'll see a list of available IRM policies; select the one you want and tap Done to apply.
Note: If the Restrict Permissions button is not enabled in your app, open any existing IRM-protected document to initialize it.
In the Android versions of Microsoft 365, any IRM-protected files that you receive will open if you are signed in with an account that has permissions to the file. When you open an IRM-protected file you will see an information bar at the top that offers to let you view the permissions that have been assigned to this file.
Information Rights Management (IRM) helps do the following:
IRM can't prevent restricted content from being: